
26 May SQL Injections- Attacks and Prevention
Structured Query Language or SQL injection is another word associated with computer hacking. It is deliberately formulated in a way that websites misinterpret it and take unintentional actions.
The goal is to spoof identity, steal the data, tamper and destroy existing data, and gain control of the database administrator.
WordPress websites seem to be the top target of cybercriminals and hackers. It is due to its huge user base that accounts for almost 40% of all websites worldwide.
The main concern is the wide range of third-party plugins that WordPress users use. However, WordPress is updating its core, but the plugins are still not under the safety net.
The biggest reason for this is the open-source ecosystem of the platform that is mainly reliant on third-party developers. Moreover, without plugins, it’s almost impossible to extend the basic functionalities of WordPress.
Well, whichever the case may be, either it is WordPress or any other website, SQL injections are detrimental to any business.
To know more about every aspect of SQL injections and how it can impact businesses, keep reading!
What is SQL Injection and How Does SQL Injection Attack Work?

If you don’t know SQL is to query, operate and administer database systems such as Microsoft SQL Server or Oracle, and so on. This database system can be attacked by the way of SQL injections.
SQL injection is one of the dangerous methods that attackers use to hack your website. It is a vulnerability that allows an attacker or hacker to interfere with the queries that an application makes to its database.
An SQL injection can read sensitive data from the backend database and can modify or delete data. Also, it can execute or administer operations, and sometimes it can also issue commands to operating systems.
Let’s try to understand SQL injection through an example below:
Supposedly, a web page authenticates a user by asking for the username and password. When the user feeds the data into it and provides the information, it is passed on to the backend database. It is done to validate the credentials provided by the user and permit access.
Now, this is the perfect opportunity for an attacker where he can supply specially crafted data through an SQL injection attack with malicious code. It may cause the application to display the contents of the user base in place of authenticating the user.
Read Also: Data Security and Protection
How Common are SQL Injections?
Many new databases use non-SQL syntax, still many are compatible with SQL. Irrespective of the intent, it is easy for anyone to access data. Thus, SQL attacks have been around us for almost two decades. But, as you dig deeper you will realize there are new attacks with a new twist.
According to IBM X-Force analysis of IBM Managed Security Services (MSS), the most commonly employed mechanism of attack against organizational networks is the injection attack.
Out of these, the common injection attack included operating system command injection (OS CMDi) and SQL injection (SQLi).
How dangerous are SQL Injections and what is the Objective of SQL Injection?
The consequences of SQL injections can be far reaching. You can see numerous consequences that have proved to be detrimental for organizations.
Right from unauthorized viewing of user lists to gaining complete administrative rights, SQL injection attack means a big compromise on data security.
Here are a few common consequences that are a result of SQL injection attack:
Authentication Bypass
When the user authentication form is vulnerable to SQL injection attacks, it allows the attacker to log into the application without providing the necessary credentials.
Gaining Complete Access to Data
SQL injection may allow the attacker to gain complete access to the data which he is not authorized for. The sensitive data may include details like passwords, credit card details, or the personal information of the user.
Manipulation of Data
Manipulating the database and building customized data views for each user is a part of an SQL injection attack. Here an attacker can use malicious codes to manipulate the backend database to gain access to the information that was not meant to be displayed.
Administrative Control of The Database
SQL injection attack can lead to complete administrative control by the attacker. The attack could be intended to delete records from the database and attack the internal network behind the firewall. It could result in the unavailability of the crucial data until the data is restored.
Read Also: Guide to SSL Certificate
What are Different Types of SQL Injection Attacks?
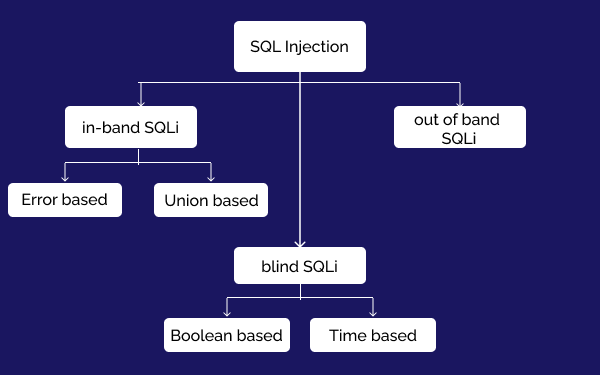
SQL injection attacks can be executed in numerous ways to cause serious issues in the organization’s network. The three major categories into which SQL injection attacks are classified are as follows:
1. In-Band SQLi
In-Band SQLi is easy to exploit and therefore the commonest of all SQL injection attacks. It occurs when a cyber attacker or hacker uses the same communication channel to launch an attack and gather results.
In-Band SQLi is further classified into two broad categories that include: Error-based SQLi and Union-based SQLi.
What is Error-Based SQLi?
Error-based SQLi is an in-band injection technique where the attacker sends SQL queries to the database intended to cause an error.
The attacker then monitors the error messages that the database server displays. This way, it gets information about the information structure of the database.
What is Union-Based SQLi?
Union-based SQLi is also an in-band injection technique where the attacker can obtain data from the database quickly.
The attacker utilizes the SQL UNION operator to combine more than one SQL command into one. Then the response that the server generates is an HTTP response.
2. Inferential SQLi
It takes longer for an attacker to attack using inferential SQLi. However, the attack carried out is dangerous as compared to other attacks.
The reason behind is that the attacker can’t see the result of an attack in-band because no data is actually transferred via a web application. Instead, an attacker can reconstruct the entire database structure.
It allows the attacker to send payloads, observing the response of the web application, and response generated by the database server.
The two types of inferential SQLi are Boolean-based Blind SQLi and Time-based Blind SQLi.
What is Boolean-Based Blind SQLi?
Boolean-based blind SQLi injection is a technique where the attacker sends SQL query to the database intended to return different results depending on the query.
The content within the HTTP response may remain the same or change depending on the Boolean result (true or false). The attacker can figure out whether the payload used is returning true or false that later on helps the attacker to enumerate the database.
What is Time-Based Blind SQLi?
A time-based blind SQLi attack is one where no data is being transferred between the database and the attacker. This way, the attacker can’t get the results easily, and thus it is called a blind injection attack. But, the attacker can make a new database structure inside a database.
The attack is intended to force a delay in the execution of queries by sending SQL commands to the server with specific codes.
Depending on the result generated (true or false) the attacker will proceed with another query.
3. Out-of-Band SQLi
Out-of-band SQLi is the commonest of all injection attacks, where an attacker can’t use the same channel to launch an attack and gather results. However, it depends on the features enabled on the database that may or may not facilitate the attack.
It is an alternative to inferential time-based SQLi attack when the server responses aren’t stable. Also, it greatly depends on the database server’s ability to make DNS or HTTP requests that give the data to the attacker.
Read Also: Guide to Penetration Testing
How to Detect SQL Injections?
SQLI is supported by various platforms that make it powerful over a huge number of sites. Its compatibility with many websites is a matter of concern and the businesses must ensure whether their site is vulnerable to SQLi or not.
But, how can you detect the SQLi vulnerability?
Routine application database audits should be your foremost priority to check whether your system is attacked by an SQLi. You can check the database for common HTML tags that have been used by worms.
If you find any, there’s a chance that your application is attacked and spreading the malware. These tags contain the IP address of malicious servers or “iframe”, “http-equiv=”refresh.””
The best way to detect an SQLi vulnerability is to examine the web pages created from dynamic content for checking any unexpected behavior.
Other things to consider include the addition of hidden iframes and code elements that are used to implant or embed one HTTP document into another in HTML.
Apart from this, the quickest way in today’s time is to use various tools online that are compatible with multiple platforms. These include sulP.biz, Netsparker, Vega, SQLMap, SQL Injection Scanner, or Appspider.
All these tools help to automate web security and identify the malicious SQL statements that the hacker executes.
How to Prevent SQL Injections?

As we discussed, most SQL injection attacks happen through user input channels. So, the best approach to control and prevent SQL injection attacks is by understanding the attack pattern.
Here are a few ways you can monitor the attacks and analyze the patterns:
1. Input Validation
The validation procedure validates whether the input given by the user is allowed or not. It considers the type, length, size, format, and other parameters to validate the input.
The value that passes the validation procedure is processed. This can be seen as an intimation or knocking before someone opens the door.
2. Parameterized Queries
Parameterized queries pre-compile an SQL statement so the statement can be executed on supplying the parameters. This way, the database can recognize the code and distinguish it from the input given by the user.
The best thing is that the user input is already quoted and thus it can’t make any changes in the intent. And, therefore, the SQL injection attack is prevented.
3. Stored Procedure
A stored procedure is a method that requires a developer to group one or more SQL statements into one logical unit. It helps them create an execution plan that allows the statements to be automatically parameterized.
We can say that it uses a code that can be stored later and used many times. So, when you don’t want to write the query over and over again, you can call for the stored procedure for execution.
4. Escaping
Another great way to prevent SQL injection attacks is escaping. Escaping is a method in which character escaping functions provided by DBMS are used for user-supplied input.
It is done to ensure that DBMS doesn’t confuse the character functions with SQL statements that are provided by the developer.
Read Also: Web Application Penetration Testing Steps
5. Web Application Firewall
A web application firewall is considered one of the best practices to identify and prevent SQL injection attacks. The firewall operates in front of the webserver via defined customizable web security rules.
It tracks the traffic which goes in and out of the web servers and analyzes the pattern. The set of rules inform the firewall about the weaknesses and behavior it should search for.
Based on this information, the firewall monitors the traffic along with the GET and POST requests. This way, it recognizes if anything could be of the potential threat and blocks it from entering the system.
We can say that the firewall is a layer of protection or a barrier between the web application and the internet.
The above prevention techniques with varying attack vectors but fail to completely protect the database. Thus, we recommend you follow some tested strategies along with the needed tools.
Taking help from a renowned agency in the cybersecurity space will help in this regard. SecureTriad is a leading Cyber Security provider based in Australia. We employ penetration testing to check for threats and suggest a suitable strategy.
Here you will get an accommodating team of professionals who will try their best to analyze the issue and suggest a suitable solution. If you are looking forward to any help or need guidance, consider checking our services right here.


