Did you know, 88% of organisations worldwide experienced phishing attempts in 2019. (Proofpoint). Lately, web application security has become a major concern for businesses of all shapes and sizes.
Web application security is referred to as safeguarding of websites, web applications, and web services from existing and emerging security threats that exploit weaknesses in application source code.
One simple flaw in the application design or misconfigured web server can potentially cause huge revenue losses. 75% of IT Leaders Lack Confidence in Their Web Application Security.
Read on to understand how web app pen testing is carried out and know more about its tools, methods, and steps.
What is Web Application Penetration Testing or Web App Pen Test?
Web application penetration testing is a process by which Cyber Security Experts simulate a real-life cyber-attack against web applications, websites, or web services to identify probable threats.
This is done in a bid to determine the current vulnerabilities that would be easily exploitable by cybercriminals. Within an organisation, web servers available locally or on the cloud are at high risk of a potential attack from malicious sources.
With penetration testing, Cyber Security Experts conduct a series of simulated attacks that replicate actual unauthorised cyber-attacks, check the vulnerability’s extent, and identify loopholes and the efficacy of overall application security posture of the organisation.
Read Also: Web Applications Security Threats and Measures to Protect
Web Application Penetration Testing Steps
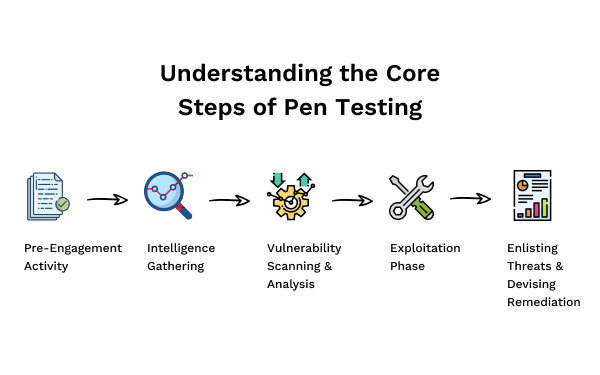
The key steps of the web application security testing process include:
Pre-engagement Activity:
Identifying the scope of work, the firm’s objectives, and the firm’s security goals are essential. At this stage, the tester also identifies the virtual and physical assets the firm uses.
The tester needs to pass the system through testing types like Blackbox testing, white box testing, Gray box testing.
Intelligence Gathering:
This step is critical in analysing the setup of the web application. This intelligence gathering is primarily divided into two types, 1st Passive Phase 2nd Active Phase.
In the Passive phase, the tester gathers information that is readily available on the internet without directly interacting with the application. For e.g., using Google syntaxes (“site:*.domain.com”) to identify the subdomains of the application or by using Wayback machine to check archived versions of the website.
The active phase is wherein the penetration tester will probe the target systems to extract useful information which can be used in further analysis. For e.g., Fingerprinting the web application to identify the version of the technology used, performing DNS lookups and zone transfers, triggering error pages, examining the source code etc.
Vulnerability Scanning and Analysis
Upon understanding the critical control points within the system, the pen tester can then minutely examine the probable attack vectors.
This involves scanning the target application for vulnerabilities using scanners such as Zed Attack Proxy (ZAP)/ Burp suite pro or Acunetix to understand how the application responds to various intrusion attempts and identify security loopholes.
The goal of the pen tester here is to determine if the vital company information is at risk.
Exploitation Phase
The data that has been collected using various exhaustive processes can now be analysed. Testing the inconsistencies while taking optimum care of the data while defining threats is important.
This step includes performing various exploitation techniques against the vulnerabilities identified during the scanning phase such as SQL injection to gain unauthorised access to the database, using brute force tools to circumvent authorisations, uploading malicious scripts to the application server to get command-line shell access.
Enlisting Threats and Devising Remediation
A complete in-depth report is generated that summarises the assessment activities carried out, the probable threats identified, the risk scorecard of the threats, and the expert recommendation advised by the pen tester.
This is then followed by conducting a retest to ensure that the designated IT team has patched the errors and the vulnerability has been eliminated.
Read Also: Importance of Security Assessments
Methodologies Commonly Used for Identifying Threats via Pen Testing
Every competent cybersecurity penetration expert uses the below-listed security testing methodologies.
OWASP (Open Web Application Security Project)
The OWASP top 10 is the regularly updated awareness document that highlights 10 most critical threats a web application may face.
OWASP is an entity that works towards strengthening the software security system by listing down the top 10 threats ranked from the highest to the lowest.
These include Injection, Broken Authentication, Sensitive Data Exposure, XML External Entities (XXE), Broken Access Control, Security Misconfiguration, Cross-Site Scripting XSS, Insecure Deserialization, Using Components with Known Vulnerabilities, Insufficient Logging & Monitoring.
The OWASP encompasses specialists across the globe who continually share knowledge on threats & attacks.
PCI DSS (Payment Card Industry Data Security Standard)
It is a set of obligations intended to ensure that all organisations that process, store, or transmit credit card information maintain a secure environment.
It improves customer trust levels and helps prevent sensitive information loss due to unassuming breaches that may happen. This is especially critical due to its link with the payment aspect.
This is considered as the gold standard globally to ensure that payment information remains secure when organisations comply with this methodology.
OSSTMM (Open-Source Security Testing Methodology Manual)
Open-source security testing is a manual for security testing that is regularly updated every six months with the latest cyber threats.
This is a systemic and scientific process conducted to help users correlate reliable penetration test reports, analyse vulnerabilities, red-teaming, and other security activities.
The range of testing included within OSSTMM include Human Security Testing, Physical Security Testing, Wireless Security Testing, Telecommunications Security Testing, and Data Networks Security Testing. Make your security testing protocol seamless with OSSTMM.
ISSAF (Information Systems Security Assessment Framework)
The ISSAF is a nine-step structured process that has been designed to evaluate systems, application control, and security of the network (Ref).
The phases that are included within the ISSAF are gathering information; mapping the network; identifying vulnerabilities; penetrating; getting basic access privileges, and then elevating them, maintaining access, compromising remote users and remote sites, hiding the tester’s digital footprints.
This type of penetration testing is rather complex as compared to the other more commonly used methodologies.
Web Application Penetration Testing Tools
While the general assumption remains that all types of penetration testing will be automated, parts of the process need to be executed manually. An ideal penetration testing brings in a combination of both manual & automated testing techniques.
Listed below are some of the most common tools used to carry out pen test.
Zed Attack Proxy (ZAP)
ZAP is one of the most popular and commonly used open source web app scanner maintained by OWASP that is used to detect vulnerabilities.
ZAP, at its core, is a ‘man-in-the-middle proxy’ meaning it stands between the pen testers browser and the target web application.
This allows the pen tester to intercept, inspect and modify the messages sent between the browser and the web application.
Burp Suite Pro
Burp suite is one of the most popular penetration testing toolkits and is often used for identifying web application security vulnerabilities.
This tool is commonly known as a proxy-based tool as it allows you to intercept communication between the browser and any target application.
This tool has some various useful and powerful features such as its ability to generate a proof-of-concept CSRF attack for a particular request, scanner with a massive database of vulnerabilities, a content discovery which allows to automatically discover content and functionality which is not visible in the application and Burp collaborator to check dangerous interactions straight out of the box.
Veracode
Veracode is a powerful static analysis tool that enables you to quickly identify and remediate application security vulnerabilities.
This tool analyses major security frameworks and programming languages without requiring the source code of the application.
This tool is helpful once it is integrated in your Software Development Lifecycle as it enables the development team to write secure code and assess the security of web, mobile, and backend applications.
Read Also: Popular Penetration Testing Tools
SQLMap
SQLMap is one of the best and widely used open-source tools to identify and exploit database-related vulnerabilities such as SQL Injection and also taking over of database servers.
This tool supports wide range of DBMS such as MySQL, MSSQL, MongoDB, Oracle, PostgreSQL so on and so forth.
Vega
Vega is another open-source web application vulnerability scanning tool. This tool can help you quickly find and validate critical issues such as XSS (cross-site scripting), SQL injections and other web app vulnerabilities that can put your application at risk.
This is a GUI based tool written in Java and is supported by major operating systems such as Linux, Windows, and OS X.
Arachni
This allows you to perform security tests on web applications and enables you to analyse, classify, identify, and record security issues within the web application.
This tool is ideal for both pen-testers and administrators. Unlike other scanners, it considers the dynamic nature of web applications, can detect changes caused while drifting through the paths of a web application’s complexity, and is able to adjust itself accordingly.
Dirb
This is one of the most useful tools when it comes to web app pen-testing. Dirb is a web content scanner. It identifies existing and/or hidden web directories in the application by launching a dictionary-based or brute-force attack against a web server. Dirb is a command-line utility, and its main purpose is to help in professional web app auditing.
Secure your organisation’s security using web application penetration testing service that helps you safeguard sensitive organisational data.
This article attempts to bring together the important aspects and components of web application penetration testing, however, this is just the tip of the iceberg. The field is quite vast and evolving rapidly with technological and operational advancements presenting better options each day.
Contact us at Secure Triad to discuss how web application penetration testing will help you to safeguard sensitive organisational data.