DDoS attacks are one of the many criminal activities that occur on the web and have the potential to bring down even the largest websites.
You can well imagine the scenario when servers get overloaded with more requests than they can handle. When the servers are unable to meet the load of junk requests, they crash and need time to restore.
Did You Know?
2020 was another breakout year for DDoS owing to the rise in DDoS activity as compared to past years. The number of DDoS attacks over 100 GB/s in volume increased 776 percent in Q1 2020.
The searches related to DDoS attack spiked and the biggest reason behind was when the biggest E-commerce giant Amazon claimed that it has brushed aside the largest DDoS attack ever reported.
This rise in the searches for DDoS attacks indicates that people are becoming aware of the attacks posed. Seeing the rise, we think that you must know everything about DDoS attacks.
Thus, we are here with this blog, where we will be discussing various aspects of DDoS attacks; so, let’s begin without further ado!
What is a DDoS Attack and How Does it Work?
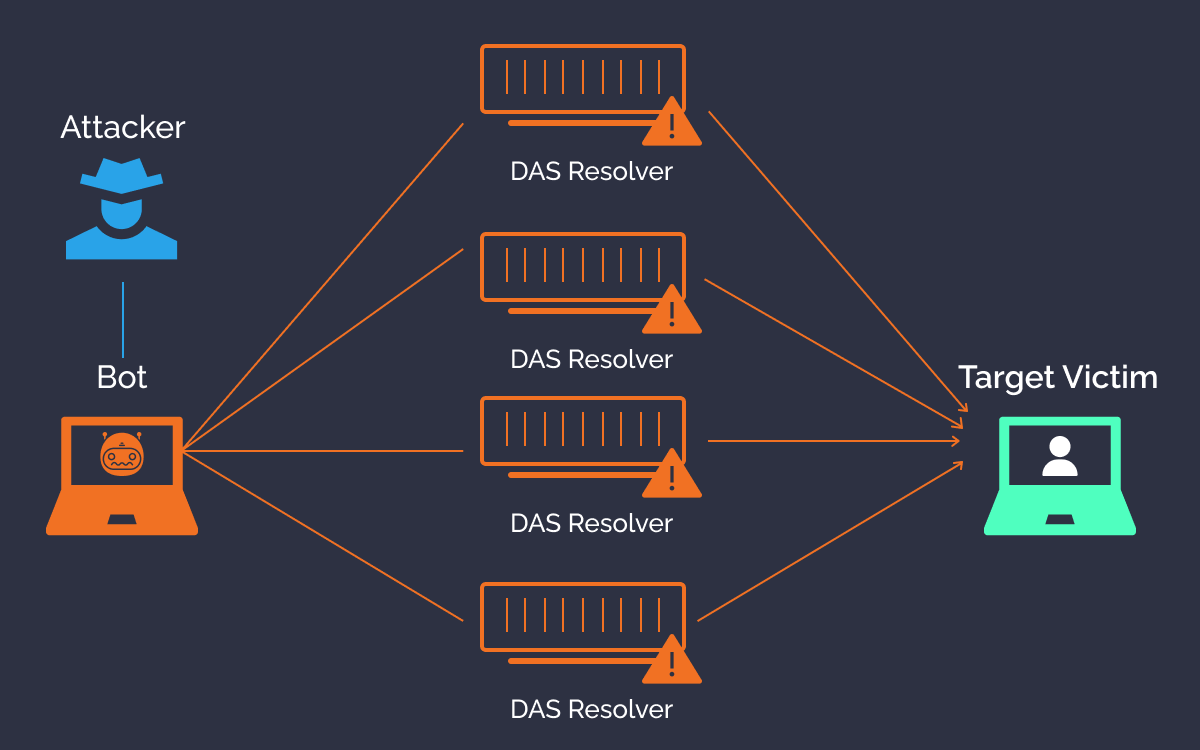
DDoS attack stands for Distributed Denial of Service, where cybercriminals flood a network with huge malicious traffic making it unresponsive and inoperative.
This clogging of the network makes even the normal traffic or legitimate packets come to a halt. And, the important thing to note here is that DDoS attacks are fueled by insecure devices and some careless practices.
However, the good thing is that we can easily tweak the practice and incorporate strict measures to ensure that DDoS attacks don’t happen on your devices.
To explain to you in simple language we are here with an example. Just imagine you are driving down a highway to get to the traffic. You are already in a rush and want to get to work as soon as possible.
During your journey to your destination, everything is smooth and crisp, but as you reach the entryway more cars join in. And, there’s no end to it as more cars keep on joining making the traffic slow to such an extent that it almost keeps the traffic on halt.
This is what happens when a DDoS attack takes place.
These DDoS attacks are common because the cyber armies are dormant until they are given orders. A specialized server called a command and control server which is typically abbreviated as a “C2” has a huge role to play. The cybercriminals order this specific C2 server to issue instructions to a compromised device.
On receiving the instructions, the insecure and compromised devices use their processing power to send fake traffic to the targeted server or website. And, this is how a DDoS attack is launched.
Read Also: Why are banks still a top target for DDoS Attacks?
What are DDoS Attacks Used For and are DDoS Attacks Successful?
DDoS attacks are usually successful owing to their distributed nature. Also, it’s challenging to figure out the difference between legitimate users and fake traffic.
However, the main purpose is not to attempt a data breach on the targeted website. Instead, it is to overwhelm the website and render it inoperable.
Well, it could be due to several reasons. Generally, it happens due to political reasons as retaliation against a company’s services.
Still, you cannot knock out the possibility of a breach because cybercriminals can use the attack as a smokescreen and attempt compromises of serious nature.
Why DDoS Attack Dangerous and What are its Implications?
When it comes to the intensity of impact that a DDoS attack can leave, then it can seriously hamper the continuity of your business. The biggest reason seems to be the heavy dependability of organisations on the internet that has become crucial for them to work.
DDoS is not only an attack but a serious threat especially for organizations like retailers, financial services, and gaming companies.
As DDoS targets the business applications, servers, and websites, the main purpose is to make the entire system inoperable on which the organizations largely depend.
It clogs the pathway with huge traffic that not only affects the daily operations but hampers productivity. All this could ultimately lead to angry customers, losing revenue, and can damage the reputation of the business.
Types of DDoS Attack?
DDoS attacks are less complicated, but they are getting advanced and growing stronger with time. The three basic categories of DDoS attack include:
- Volume-based attacks that use high traffic to inundate the network bandwidth.
- Protocol attacks are the ones that emphasize exploiting the server.
- Application-based attacks target the application and considered a more serious type of attack.
Based on the above three broad categories while considering the volume of traffic and targeted vulnerabilities, there are many attacks carried out by cybercriminals.
Here are a few of them:
SYN Flood
SYN flood is the one that targets the weaknesses in the TCP connection sequence. Then it begins the attack which is called the handshake on receiving an SYN (synchronized) message from the host machine.
The server later acknowledges the message and sends an ACK (Acknowledgement) to the initial host that closes the connection.
UDP Flood
UDP stands for User Datagram Protocol, which is a type of networking protocol. It targets random ports on a computer or network using UDP packets. Here the host checks for the applications that address those ports.
Read Also: Guide to Penetration Testing
HTTP Flood
HTTP flood is the type that seems legitimate GET or POST requests. The hacker exploits these GET or POST requests. Also, the attack uses less bandwidth to be launched but can make the server use more resources.
Ping of Death
Ping of Death is a type of attack that sends malicious pings to a system with the intent to manipulate the IP protocols. However, this attack has become less effective in today’s time.
Smurf Attack
Smurf attack uses a malware program called smurf to exploit Internet Protocol (IP) and Internet Control Message Protocol (ICMP). It uses an ICMP to spoof an IP address to which it pings on a given network.
Fraggle Attack
The Fraggle attack is another type of DDoS attack that blocks a router’s broadcast network by using a large amount of UDP traffic. However, it is the same as a smurf attack, but the only difference is that it uses UDP rather than ICMP.
Contact here for Web Application Penetration Testing
Application Level Attacks
Another type of DDoS attack is the application-level attack that targets and exploits the vulnerabilities in an application. It doesn’t target the entire server, but an application that has a few known weaknesses.
Zero-Day DDoS Attack
A zero-Day DDoS attack is a new type of attack that is more advanced and targets the vulnerabilities that haven’t been patched.
Read Also: SQL Injection Attack
How Long Does DDoS Attack Last?
DDoS attacks vary in time length depending on the severity of the attack. It can last from a good 24 hours to around two weeks.
Is it Difficult to Prevent a DDoS Attack?
Since DDoS attacks are of distributed nature, it is challenging to prevent. The main issue that arises is that the organizations can’t figure out the difference between legitimate web traffic and a fake one.
It clogs everything with huge traffic by sending requests that are a part of a DDoS attack. Still, you can take some countermeasures to ensure that a DDoS attack doesn’t happen to your organization.
We have discussed a few measures in the section below, let’s have a look.
How Can You Stop DDoS Attacks?
1. Identify that DDoS Attack Has Been Launched
The first thing that any organization has to do is to identify that it is under attack especially if it runs its servers. The sooner you can identify the issue the better it would be.
The wisest thing you can do is to familiarize yourself with the inbound traffic as it will be easier for you to spot the issues.
2. Develop a Response Plan
You should undertake a thorough security assessment of your entire network and develop a DDoS response plan based on it.
The reason we are recommending you develop a plan is that when a DDoS attack happens, you will hardly get any time to think about doing anything. Thus, you need to define a proper strategy so you can take prompt reactions and avoid any damage.
It is best to consider the infrastructure before you make a plan because complex security and network infrastructure can make the plan quite exhaustive. Ensure that your data is prepared, and the team is well aware of the attack.
You can do the following:
- Prepare system checklist to ensure implementation of filtering tools and security-enhanced hardware.
- Form a quick response team to ensure organized reaction.
- Define procedures and enable quick notification. Ensure that you have a proper channel of communication so your team would know who to connect with in case the attack is launched.
Also, keep a list of internal as well as external contacts that you can take help from. Inform your contacts and get in touch with your cloud service providers or security vendors.
Read Also: Penetration Testing Tools
3. Give More Bandwidth to Your Server
If you give more bandwidth to the server, it can accommodate more traffic. Also, if there is any unexpected traffic surge, there would be no issue of blocking the pathway.
As we discussed in the point above that you should familiarize yourself with the type of traffic, you will know from where the traffic is coming whether it is from an advertising campaign or any special offer.
Considering the traffic sources you can give more bandwidth to the server. You may still have a DDoS attack launched, but you will surely have a few extra minutes to act before your resources are at risk.
4. Practice Basic Security
Another best thing you can do is to ensure that the users in the organization make the least possible error. Indulge in strong security practices and educate your employees so that nothing gets compromised when it comes to the security of the system.
Ensure that everyone uses complex passwords that cannot be guessed easily, force the users to change the passwords regularly, and implement secure firewalls to block unnecessary outside traffic.
All these security measures could be considered as a strong foundation that will help to prevent DDoS attacks.
5. Beware of the Warning Signs
You must check for the obvious warning signs to prevent DDoS attacks. The signs may include network slowdown, connectivity issues in the company intranet, website shutdown, prolonged issues with the server, and more. If you feel any unexpected change, you must take the right action.
6. Look for a DDoS Mitigation Service
It is wise to choose a DDoS mitigation service that tracks the traffic on the website and applications continuously. They have dedicated engineers and administrators to take faster action and save your organization from any disaster.
Ensure that the service provider helps you with a comprehensive mitigation plan that gives better protection against DDoS attacks in future.
Secure Triad is one such agency that can help you with a smart plan against DDoS attacks. It is one of the renowned penetration testing service providers, which is based in Australia.
The company has an accommodating and dedicated team of experts that will help you ensure business continuity.
If you are facing any issues and want to enhance your cybersecurity, consider contacting our security experts. Call us here to find out more about DDoS attacks and what we can do for you.